If we are going to use OIDC (OpenID Connect), we have need to know the definitions of OAuth and OIDC. Because OAuth is for authorization and OIDC is on top of OAuth to provide authentication. So, OIDC is providing authorization and authentication.
What is OAuth?
What is OAuth?
The OAuth 2.0 authorization framework enables third-party applications to obtain limited access to a web service.
[To see more on OAuth itwithcs.blogspot.com: Click here]
What is OpenID Connect?
OpenID Connect is a simple identity layer on top of the OAuth 2.0 protocol. It allows Clients to verify the identity of the End-User based on the authentication performed by an Authorization Server, as well as to obtain basic profile information about the End-User in an interoperable and REST-like manner.It uses simple JSON Web Tokens (JWT), which you can obtain using flows conforming to the OAuth 2.0 specifications.
What are Identity Servers?
Identity server are the core part of any identity and access control infrastructure. It is the central database that stores user credentials. The identity servers are the server that all IT resources check with authenticate user access..
Example: IdentityServer [http://identityserver.io/], Auth0 [https://auth0.com/], WSO2 Identity & access management [https://wso2.com/], etc.
[To see more on OAuth itwithcs.blogspot.com: Click here]
What is OpenID Connect?
OpenID Connect is a simple identity layer on top of the OAuth 2.0 protocol. It allows Clients to verify the identity of the End-User based on the authentication performed by an Authorization Server, as well as to obtain basic profile information about the End-User in an interoperable and REST-like manner.It uses simple JSON Web Tokens (JWT), which you can obtain using flows conforming to the OAuth 2.0 specifications.
What are Identity Servers?
Identity server are the core part of any identity and access control infrastructure. It is the central database that stores user credentials. The identity servers are the server that all IT resources check with authenticate user access..
Example: IdentityServer [http://identityserver.io/], Auth0 [https://auth0.com/], WSO2 Identity & access management [https://wso2.com/], etc.
Note: Here I have used Auth0 universal identity platform to build an OIDC application. [More user friendly because of the direct functionality]
How the OIDC works?
For example, if you chose to sign in to Auth0 using your Google account then you used OIDC. Once you successfully authenticate with Google and authorize Auth0 to access your information, Google will send back to Auth0 information about the user and the authentication performed. This information is returned in a JSON Web Token (JWT). You'll receive an Access Token and, if requested, an ID Token.
+--------+ +--------+ | | | | | |---------(1) AuthN Request-------->| | | | | | | | +--------+ | | | | | | | | | | | End- |<--(2) AuthN & AuthZ-->| | | | | User | | | | RP | | | | OP | | | +--------+ | | | | | | | |<--------(3) AuthN Response--------| | | | | | | |---------(4) UserInfo Request----->| | | | | | | |<--------(5) UserInfo Response-----| | | | | | +--------+ +--------+
- The RP (Client) sends a request to the OpenID Provider (OP)
- The OP authenticates the End-User and obtains authorization.
- The OP responds with an ID Token and usually an Access Token.
- The RP can send a request with the Access Token to the UserInfo Endpoint.
- The UserInfo Endpoint returns Claims about the End-User.
OIDC JWT (JSON Web Token)
Access Token
Access Tokens are credentials that can be used by an application to access an API. Access Tokens can be an opaque string, JWT, or non-JWT token. Its purpose is to inform the API that the bearer of this token has been granted delegated access to the API and request specific actions (as specified by the scopes that have been granted).
ID Token
The ID Token is a JSON Web Token (JWT) that contains identity data. It is consumed by the application and used to get user information like the user's name, email, and so forth, typically used for UI display. ID Tokens conforms to an industry standard (IETF RFC 7519) and contain three parts: a header, a body and a signature.
Claims
JWT Tokens contain claims, which are statements (such as name or email address) about an entity (typically, the user) and additional metadata.
Claims
JWT Tokens contain claims, which are statements (such as name or email address) about an entity (typically, the user) and additional metadata.
Note:The OpenID Connect specification defines a set of standard claims. The set of standard claims include name, email, gender, birth date, and so on. However, if you want to capture information about a user and there currently isn't a standard claim that best reflects this piece of information, you can create custom claims and add them to your tokens.
Let's Create a Regular Web Application in Auth0
My next blog will continue with the sample application 'How the real world OIDC flow is working on top of OAuth.
Let's Create a Regular Web Application in Auth0
- Create a user account in Auth0 and create your own Tenant [eg: benjamin.auth0.com]
- Provide the information about the created Tenant
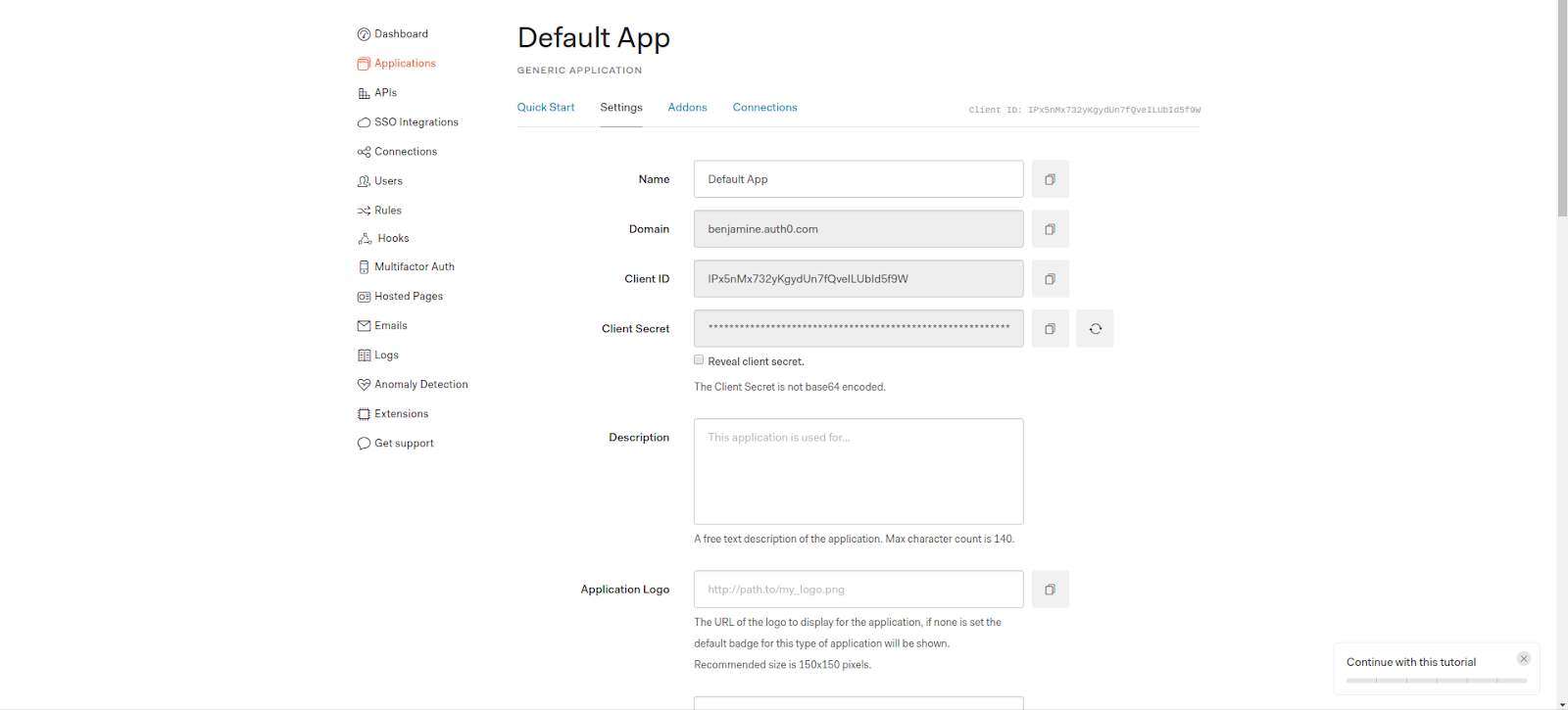
- Navigate to the dashboard and click on the Applications menu option on the left. Clicking the + Create Application button
- Setting:
- Application Type: Regular Web Application
- Token Endpoint Authentication Method: POST
- Allowed Callback URL: http://localhost:9090/oidcapp/callback [Your own application callback URL]
- JWT Expiration (seconds): 360 - 5min
- You can get the ClientID and Client Secret of the created application
- Make sure about the OAuth endpoints [Advance --> Endpoints].
- Set the algorithm used for signing your JSON Web Tokens.
- Create a new user who can be able to login to the created application and this will be the sharing information.
- After create the application and follow the above mentioned settings you can able to see new web API created with the application name. [Dashboard --> API]
My next blog will continue with the sample application 'How the real world OIDC flow is working on top of OAuth.










Comments
Post a Comment